Staminus hack: 2,300 customers impacted as CEO admits cyberattack

Matt Mahvi, the chief executive of Staminus Communications, has admitted that hackers were able to breach his firm's network, take the website offline and compromise sensitive customer data including passwords and payment card records.
The California-based company is a web-hosting service that offers protection against website-crippling distributed denial of service (DDoS) cyberattacks, however, on 10 March the firm was successfully targeted by a hacking collective. "A rare event cascaded across multiple routers in a system wide event, making our backbone unavailable," Staminus initially wrote to its customers.
Now, the firm's CEO has elaborated on the scope of the attack and it's much worse than previously reported. "We can now confirm the issue was a result of an unauthorised intrusion into our network," Mahvi said in a statement.
"As a result of this intrusion, our systems were temporarily taken offline and customer information was exposed [...] we believe that usernames, hashed passwords, customer record information, including name and contact information, and payment card data were exposed.
"While the exposed passwords were protected with a cryptographic hash, we also strongly recommend that customers change their Staminus password."
According to Mahvi, customers should now beware of potential phishing scams. "Any email correspondence we may send regarding this matter will not contain a link, so if you receive an email appearing to be from us that contains a link, it is not from us, and you should not click on the link," he warned.
The CEO said that 'additional measures' have now been put in place to harden security and help prevent a future attack however he did not clarify what these were. Mahvi said his firm will be cooperating with law enforcement in any subsequent investigation.
Within 24 hours of first reporting network issues and outages, sensitive internal company data from Staminus started to appear online. The leak, since posted in full via Tor, contained over 15GB worth of database data stolen from both Staminus and a related anti-DDoS website called Intreppid. Interestingly, one of Staminus' customers was hate group the Ku Klux Klan and as a result its website was also taken offline.
Scope of the breach
Risk Based Security (RBS), a US security and consultancy group has said there are roughly "2,300 previous and current" Staminus clients impacted by the breach. These range from companies that also provided internet hosting services to hobby websites for individuals, the firm said.
Furthermore, detailed analysis by RBS states the data dump includes:
- Credit card table contains 2,042 records with full card details.
- Billing table contains 141,403 tracks of account billing from purchases.
- Account table contains 4,415 users' details with full addresses, contact details, company details, emails, and encrypted passwords.
- Staff details with encrypted passwords, email addresses, and Oauth credentials in the format of tokens and generated user keys.
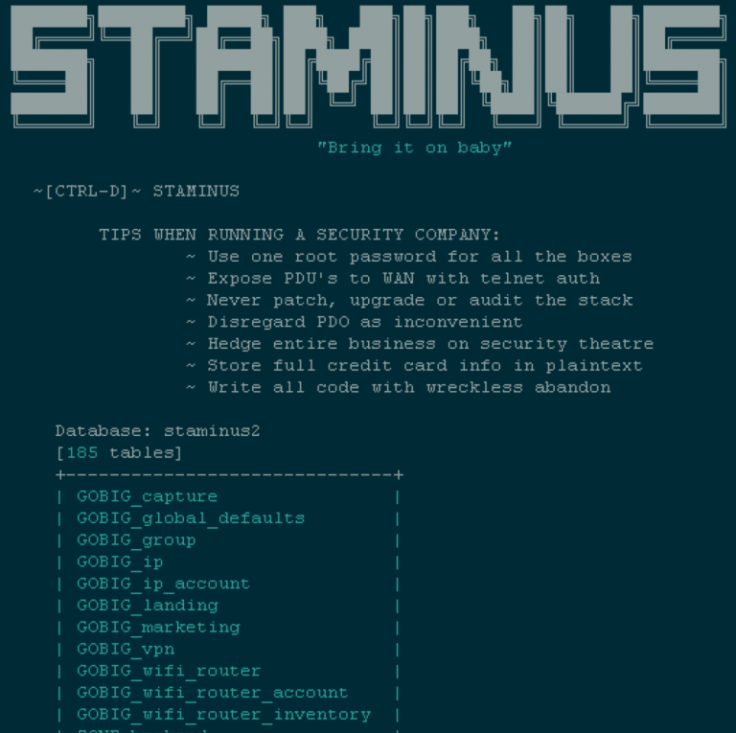
At the time of the breach, the data dump that was posted online and viewed by IBTimes UK contained a personal note from the hackers titled 'Tips when running a security company'. It listed a number of alleged faults that allowed the breach to occur, including: "Store full credit card info in plaintext, use one root password for all the boxes, never patch, upgrade or audit the stack and write all code with wreckless [sic] abandon."
© Copyright IBTimes 2025. All rights reserved.






















