Telegram messaging app makes it easy for someone to stalk you, says security researcher

The encrypted messaging app Telegram that is beloved by Islamic State (Isis) terrorists and privacy-conscious users actually isn't really that secure – security researchers have revealed that the app makes it easy for attackers to stalk other users.
Ola Flisbäck, a consultant at Sony Mobile Communications, has demonstrated that although Telegram claims to protect users' data and conversations from "snooping third parties" such as governments and advertisers, the app is actually leaking huge amounts of metadata that make it possible to gain information about Telegram users.
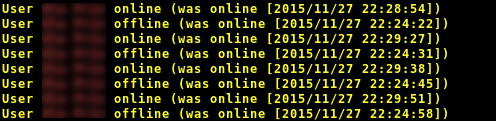
The metadata includes information about when a user comes online and is using the app, and this data is sent to the smartphones of all a user's contacts on Telegram. Although the data is not visible to a regular user just using Telegram on their phone, the metadata is accessible to command-line clients and all of the information is listed neatly in clear text.
"The Telegram android app sends a notification to all contacts when it becomes or stops being the 'foreground' app on the device. Using that information alone it's at times easy to make guesses about who's talking to who if you have several contacts in common with a 'victim'. An 'attacker' will sometimes see the victim and another contact taking turns going active/inactive as they pass messages back and forth," Flisbäck wrote on GitHub.
Added to that, if the attacker has your mobile number, they can add you as a contact on Telegram without your knowledge and instantly start receiving metadata from your phone when you come online.
"The metadata may be a considerable problem in itself but what makes it worse is that Telegram does not require contacts to mutually agree that they should be connected! As long as an attacker knows the phone number of the victim and add it to the android contacts the victim will show up as a Telegram contact and the attacker will automatically subscribe to the victim's metadata," added Flisbäck.
"As a bonus the victim will not be notified in any way and the attacker will not show up among the victim's Telegram contacts."
Telegram spokesperson Markus Ra told IBTimes UK that users can hide their "last seen" time from other users by modifying its privacy and security settings, and that this works at the API level so even attackers will be unable to access the metadata.
Flisbäck's findings come less than two weeks after operations security expert the grugq posted on Medium about the many problems he has with Telegram, which include the fact that Telegram uploads a user's entire phone contacts database to Telegram's servers in order to build a giant social map of who knows who.
The grugq also complained about the metadata being exposed on both iOS and Android devices; and the difficulty in setting up Secret Chats on the phone, which means that many users might think that they are having conversations that are encrypted end-to-end, but actually the conversations are not secure because the user hasn't gone through the multi-step process to set up the Secret Chat properly.
© Copyright IBTimes 2025. All rights reserved.






















