TopHat campaign: Hackers target Middle East using malware-laced Arabic files about political events
The TopHat campaign seemed to have begun in September 2017, researchers observed.

Security researchers have detected a fresh wave of attacks targeting users in the Middle East that leverage popular third-party services such as Google+, Pastebin and bit.ly. According to researchers at Palo Alto Networks Unit 42, hackers have been using Arabic language documents related to current political events as lures to dupe curious victims into downloading and running malicious malware.
"The ultimate payload is a new malware family that we have dubbed 'Scote' based on strings we found within the malware samples," researchers said in a blog post published on 26 January. "Scote provides backdoor access for an attacker and we have observed it collecting command and control (C2) information from Pastebin links as well as Google+ profiles.
"The bit.ly links obscured the C2 URLs so victims could not evaluate the legitimacy of the final site prior to clicking it. We are calling their recent activity the 'TopHat' campaign."
The TopHat campaign seemed to have begun in September 2017. In some instances, the original filenames of the samples identified by the researchers were written in Arabic.
Hackers deployed the malware using four techniques - two using malicious RTF files, one leveraging self-extracting Windows executables and the fourth using RAR archives.
The first technique involves a malicious RTF that makes an HTTP request to dubious website. In this case, researchers observed most of the activity taking place in late October 2017 with majority of the downloads originating from the Palestinian Territories and the United Arab Emirates.
The second RTF technique exploited CVE-2017-0199 – a Microsoft Office/WordPad remote code execution (RCE) vulnerability that was patched by Microsoft in September 2017. Once the RTF file is opened, a lure message in Arabic pops up that is related to an event that took place in August when Palestinian President Mahmoud Abbas announced plans to convert a presidential palace into a national library.
"This is consistent with the timeline of the attacks we witnessed, as the event took place roughly a week before we observed these malware samples," researchers noted. Meanwhile, the downloaded file with a RTF extension – which is actually a VBScript – executes a PowerShell command to download and execute the malware.
Another technique leveraged a unique tactic that researchers said they haven't seen before. It uses an attack called "Don't Kill My Cat" or DKMC that allows the attacker to load a legitimate bitmap (BMP) file that includes shellcode within it.
The final technique uses self-extracting executable files to download a phony document onto the user's computer and deploy the malware.
"When the malware is run it will drop a file with an original filename of 'abbas.rtf'," researchers said. "The decoy document used discusses the potential dissolving of the Palestinian Authority (PA) by the President Mahmoud Abbas. This particular event was reported on August 23, 2017, just before Trump administration officials were set to visit Ramallah."
Based on the techniques used and content of the dubious documents, researchers believe "at least some of the targeted victims" are likely located in the Palestinian territories. The new Scote malware family uses various tricks and tactics to evade detection but, so far, "provides relatively little functionality to the attackers once deployed," researchers said.
"This may well be due to the fact it is still under active development," they added.
Hackers often exploit interest in current events and popular trends in their cyberattacks, particularly those that are widely covered, when targeting users around the world. In this campaign, some Google+ profiles that were used to deliver the malware contained the name "Donald Trump" while other topics referred to President Abbas.
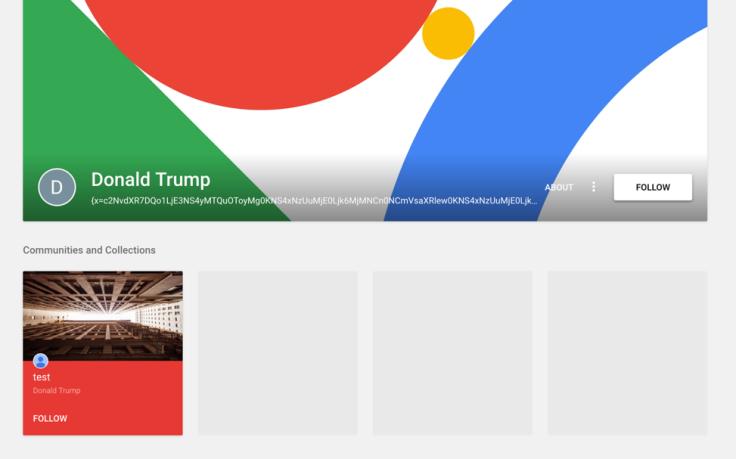
"In the TopHat campaign, we have observed yet another instance where a threat actor looks to be using political events to target individuals or organizations within the Palestine region," researchers said.
"The TopHat campaign was found to have some overlaps discovered with the previously reported DustySky campaign when the attacker was identified to be submitting their files for testing purposes. Unit 42 will continue to track and monitor this threat and will report on any developments that occur."





















