Two banking Trojans that can plunder your accounts are on the rise, Microsoft warns
The malware variants – dubbed Qakbot and Emotet – are "information stealers".

The use of two notorious strains of banking Trojan that are able to silently infect computers, steal login details and empty accounts has spiked in recent months, Microsoft warns.
The malware variants – dubbed Qakbot and Emotet – are known as "information stealers" and, while technically separate, they share a number of key behavioural similarities.
According to a blog post published Monday (6 November), some of the new strains in use by hackers have worm-like capabilities that let them quickly spread across infected computer networks.
Both variants can also log a victim's keystrokes, send files to a cybercriminal's command and control server, and hijack internet cookie and certificate data.
The worm functionality, adopted after the WannaCry ransomware outbreak in May, was also noted by SophosLabs in August. Essentially, they have both evolved into effective tools for financial cybercrime.
"Over the years, the cybercriminals behind Qakbot and Emotet have improved the code behind their malware," the researchers stated. "They have evolved to evade detection, stay under the radar longer, and increase the chances of spreading to other potential victims."
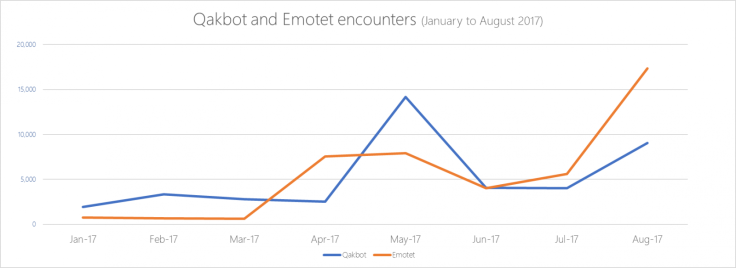
New analysis, from January to August this year, suggested both Trojans were getting better at hitting targets. At the start of 2017, Emotet infections were minimal – well under 5,000 detections.
Yet in August, Microsoft encountered the malicious software on machines more than 15,000 times.
Experts found that – like WannaCry – it could take advantage of a Windows OS protocol known as Server Message Block (SMB) to "drop copies" of the malware onto linked computers.
"The threat to information is greater than ever," Microsoft warned, also showing statistics indicating that home internet users make up a large chunk of the target demographic for the culprits.
Emotet was first discovered to be a major banking Trojan threat by security firm Trend Micro back in 2014. Cybersecurity expert Joie Salvio wrote at the time: "What makes this malware, detected as Emotet, highly notable is that it 'sniffs' network activity to steal information."
Microsoft released a number of key tips so users can stay protected against the threat:
- Cut off internet access or disconnect the affected computers from the network until cleaned.
- Stop sharing folders that show signs of infection or set shared folders to read-only.
- Practice credential hygiene. Remove unnecessary privileges, or disable privileged accounts that have been observed to spread malware using SMB.
- Update all security software on your computer system as soon as possible.