'We are digging our own grave' – Russian Dark Web criminals on the dangers of selling ransomware
In the aftermath of WannaCry, administrators of underground cybercrime forums are now rethinking the ethics and risks of ransomware dealing.
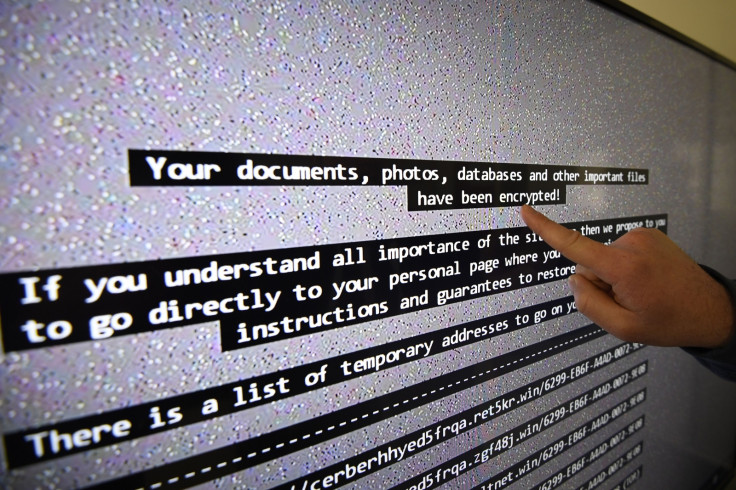
Ransomware attacks have dominated cyberspace over the past few years. The nature of the attacks, limited effort required to launch them, as well as the possibility of making a quick buck attracted numerous cybercriminals to ransomware. However, in the wake of massive global ransomware epidemics such as WannaCry and NotPetya, dark web cybercriminals operating underground forums, especially Russian ones, are now rethinking the ethics and risks of dealing ransomware.
Administrators of Russian dark web and other underground cybercrime communities are now grappling with the ethical dilemma of selling ransomware willy-nilly. According to researchers at Flashpoint and Anomali, who analysed discussions of various prominent dark web admins, there appears to be a growing concern among cybercriminals about ransomware attacks.
Researchers noted that on such discussion, one dark web cybercriminal suggested banning ransomware.
"It attracts attention to malware and causes companies to introduce measures to increase their security. It increases general awareness of topics related to information security. It's a business which is built not on intelligence and mental dexterity, but on brute-force and luck," the cybercriminal said. "Allowing ransomware operators on the forum, we are digging our own grave. Of course, banning this work on the forum doesn't stop this type of business, but as a minimum we can use community disapproval to make it more difficult to enter into it."
Researchers said that the cybercriminal's post on a proposed ransomware ban elicited numerous responses, with nearly 48% supporting the ban.
In another post, a highly regarded member of a top-tier Russian cybercrime forum wrote, "from the bottom of my heart, I sincerely wish that the mothers of all ransomware distributors end up in the hospital, and that the computer responsible for the resuscitation machine gets infected with [the ransomware]..."
However, not all were in favour of abandoning such a lucrative business.
Another cybercriminal suggested that the use of ransomware should be an individual decision and that as long as the attacks don't harm Russia, anything goes. "There is only one rule – don't target Russia. All other cases depend on one's degree of perversion. Some people take grandma's last 10k, some encrypt a corporate company and ransom [their files] for 2k, some brute-force Wordpress control panels, upload shells and then send spam or host their own malware, some install skimmers. Everyone has their own thing."
These discussions provide an insight into the Russian underground cybercrime community.
"It's very important to note that underground administrators are incredibly powerful in the DDW. Regardless of whether administrators are revered or reviled, the community respects their decisions. Those who don't comply with such decisions risk being exiled from the forums or even doxed," Anomali and Flashpoint researchers said in a joint report.
The discussions indicate that the aftermath of ransomware attacks, as well as the increased scrutiny from law enforcement authorities may have prompted cybercriminals to rethink the pros and cons of using ransomware. Although it is unlikely that ransomware may be completely abandoned by cybercriminals, this direction may prompt other attackers to think twice before using ransomware or chose their targets more carefully. However, given the highly adaptive nature of cybercrime, it is likely that attackers may come up with new and more advanced ways to go after desired targets.
© Copyright IBTimes 2025. All rights reserved.






















