What is Bateleur? New backdoor Trojan attack by Carbanak hacking group targets restaurant chains
The JavaScript backdoor has a wide range of capabilities including taking screenshots and stealing passwords.

Security researchers have discovered that the notorious hacking group Carbanak has added a new JavaScript backdoor called Bateleur to its nefarious toolkit used to target restaurant chains across the US. The hacking outfit, also referred to as FIN7, has been previously known to target financial institutions, hospitality organisations, retailers, merchant services and suppliers among others.
Active since 2013, the criminal operations has also stolen $1bn from banks worldwide in 2015 and has used APT-style techniques along with various malware to attack organisations.
According to security firm Proofpoint, the group has been using phishing emails and macro-laden documents to drop the backdoor Trojan Bateleur in an effort to infiltrate restaurants' networks.
Named after a breed of Eagle, the malicious backdoor Bateleur features a wide range of robust capabilities including taking screenshots, stealing passwords, executive custom commands and PowerShell scripts and even the ability to uninstall and update itself.
"Starting in early June, we observed this threat actor using macro documents to drop a previously undocumented JScript backdoor, which we have named "Bateleur", instead of dropping their customary GGLDR payload," Proofpoint researchers said. "Since its initial sighting, there have been multiple updates to Bateleur and the attachment macros.
"The new macros and Bateleur backdoor use sophisticated anti-analysis and sandbox evasion techniques as they attempt to cloak their activities and expand their victim pool."
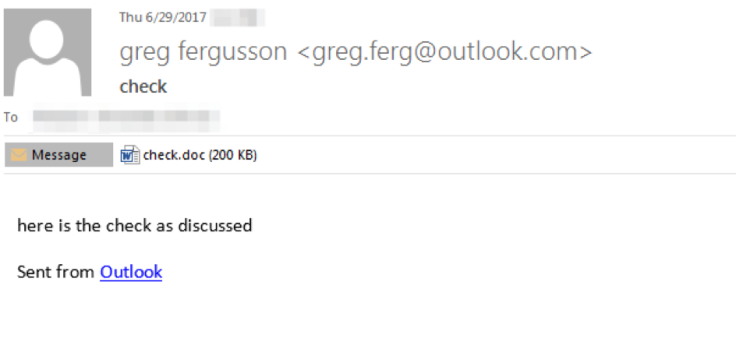
The group uses phishing emails from an Outlook or Gmail account with a simple lure and a macro-laden Word document to infect its victims. The message claims to contain information about a previously discussed check in the attached document.
It also claims that the attached document is encrypted and is protected by either "Outlook Protect Service" or "Google Documents Protect Service", depending on the email account the lure message has been sent from. If a user enables editing of the document, the names of numerous authentic antivirus companies appear on the JScript document dropper, tricking the victim into thinking that the file is secure.
The document then accesses the malicious payload and executes a series of scheduled tasks to run Bateleur in an attempt to evade detection.
Researchers said some of Bateleur's other capabilities include "anti-analysis (obfuscation), retrieval of infected system information, listing of running processes, execution of custom commands and PowerShell scripts [and] loading of EXEs and DLLs." It also has anti-sandbox functionality, however, the group does not seem to have used those features so far, they noted.
It also lacks other features such as backup servers and an additional module from the command and control server to be able to exfiltrate passwords. However, Proofpoint expects that these will be added in the "near future."
In less than a month, researchers said the backdoor has been updated from version 1.0 to 1.0.4.1, adding several new commands.
"We continue to see regular changes to the tactics and tools used by FIN7 in their attempt to infect more targets and evade detection", researchers said. "The Bateleur JScript backdoor and new macro-laden documents appear to be the latest in the group's expanding toolset, providing new means of infection, additional ways of hiding their activity, and growing capabilities for stealing information and executing commands directly on victim machines."
© Copyright IBTimes 2025. All rights reserved.





















