What is Spider ransomware? New malware threatens to delete your files in 96 hours unless you pay up
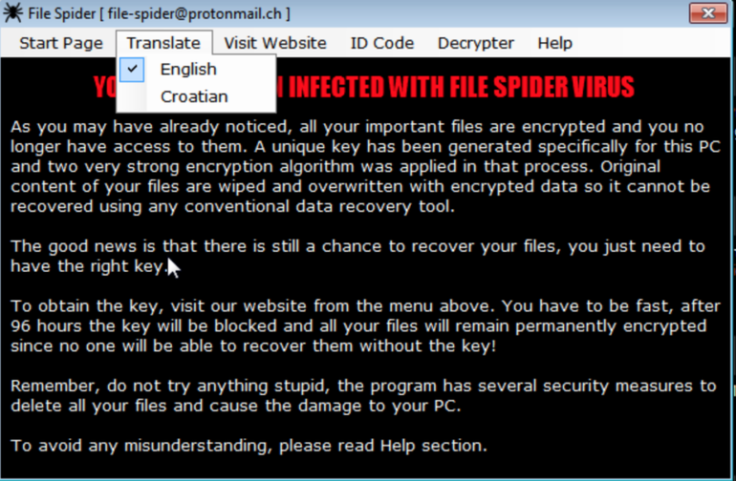
"Remember, do not try anything stupid," the ransom note warns.

Security researchers have discovered a new ransomware that encrypts files and gives victims a 96-hour deadline to pay up. Experts at Netskope Threat Research labs discovered the new "mid-scale" campaign on 10 December that is still ongoing.
Targeting users in the Balkans, including the Bosnia and Herzegovina region, the campaign involves phishing emails written in the Bosnian language with the subject line reading, "Debt Collection." The email includes a malicious Office document attached that contain obfuscated code.
Once executed, a Windows PowerShell launches to download the ransomware payload from a host website. The PowerShell script then decodes the Base64 string and performs operations to decode the final payloads that are saved as executable files. These .exe files contain the ransomware encryptor.
After the PowerShell launches the encryptor, the malicious code encrypts the user's files, adds a "spider" extension and displays the ransom note. The Spider ransomware decryptor also monitors the infected system's processes and prevents the user from quickly opening any windows utility tools such as taskmgr, msconfig, regedit, cmd, outlook, winword, procexp, excel or msaccess.
"Original content of your files are wiped and overwritten with encrypted data so it cannot be recovered using any conventional data recovery tool," the ransomware note, which is available in two languages, reads. "The good news is that there is still a chance to recover your files, you just need to have the right key."
The hackers threaten to permanently delete the user's files if they don't receive payment within 96 hours.
"Remember, do not try anything stupid," the ransom note warns. "The program has several security measures to delete all your files and cause damage to your PC."
The threat actors even provide instructions on how to download and use the Tor browser to access the payment site as well as how to purchase Bitcoin for the ransom. If a user is still confused about the process, a "help section" and a link to a tutorial video on decrypting files is also provided.
"The video provides instructions to decrypt victims files. We suspect that the video was most likely uploaded by the threat actor group of Spider," Netskope researchers said.
Researchers say ransomware will continue to grow as a nefarious and profitable tool for hackers to target organizations, businesses and users across the globe.
"We continue to see an increase of decoy Office documents as an attack vector in spreading ransomware like GlobeImposter tied to several active and ongoing campaigns," researchers said. "As ransomware continues to evolve, administrators should educate employees about the impact of ransomware and ensure the protection of the organization's data by making a regular backup of critical data.
"In addition to disabling macros by default, users must also be cautious of documents that only contain a message to enable macros to view the contents and also not to execute unsigned macros and macros from untrusted sources."





















