Would you fall for this iOS phishing scam? Rogue pop-ups can hijack your Apple passwords
How do you steal someone's Apple ID password? It may be easier than you think...
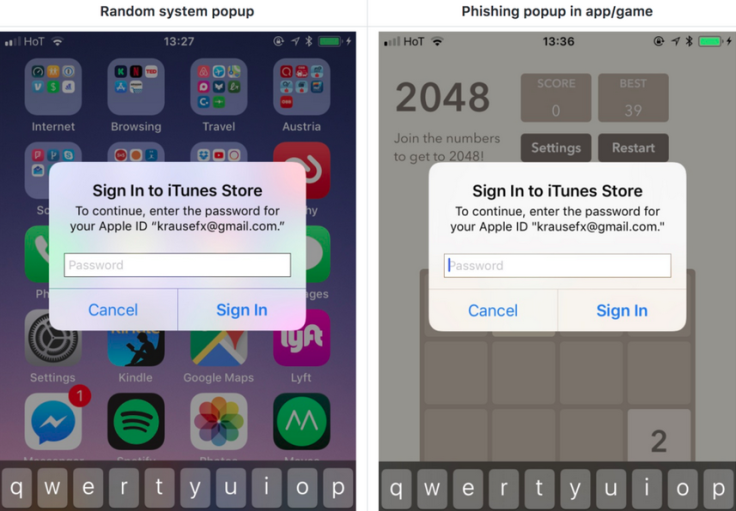
How do you steal someone's Apple ID password? Well, have you tried asking nicely?
That was the subtle approach taken by Apple iOS code researcher Felix Krause, who this week (Tuesday 10 October) published a blog post showing just how easy it is to create a convincing login form and steal victims' personal credentials via standard phishing tactics.
The 'Sign in to iTunes' form looks almost identical to the one that regularly pops up on iPhones and iPads.
According to Krause, it took roughly 15 minutes to create. Not that you should attempt to use the proof-of-concept in real life: that would be very illegal.
In any case, the researcher warned that it was "shockingly easy" to replicate the form.
Apple's operating system frequently asks users for passwords, including when they need to install urgent security updates or upgrade to new software.
Krause said that the majority of users would willingly input their passwords without question.
He wrote: "Users are trained to just enter their Apple ID password whenever iOS prompts you to do so. Those popups are not only shown on the lock screen, and the home screen, but also inside random apps." He said this could "easily be abused" by rogue app developers.
"Even users who know a lot about technology have a hard time detecting that those alerts are phishing attacks," he warned on his website.
He continued: "Showing a dialog that looks just like a system popup is super easy, there is no magic or secret code involved, it is literally the examples provided in the Apple docs, with a custom text." He said that creation of the form took under 30 lines of coding.
Would you be able tell the difference between the real and the fake?
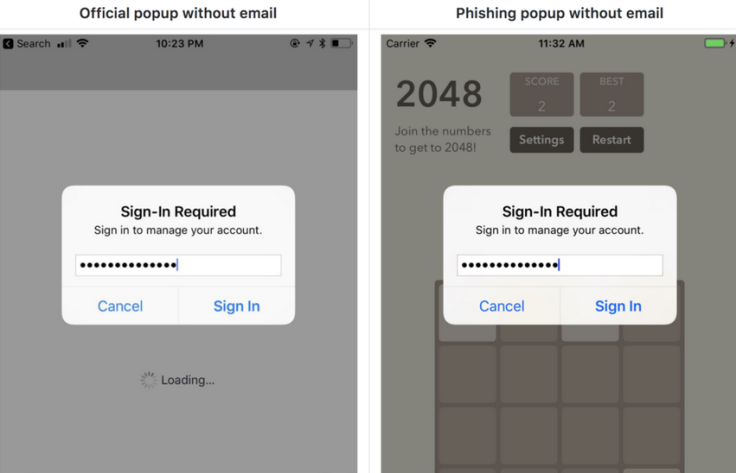
Of course, there are subtle differences, but on Twitter Krause said there was nothing in the code that couldn't be adapted with little effort. Unfortunately, he asserted that even Apple accounts with two-factor authentication would still be vulnerable to the phishing attack.
"What if the app asked you for your 2 step code?" he wrote. "Most users would gladly request a 2FA-token and ask for it, and directly pipe it over to a remote server."
Luckily for you, Krause noted that there are a number of ways to recognise the attack:
• Hit the home button, and see if the app quits
• If it closes the app, and with it the dialog, then this was a phishing attack
• If the dialog and the app are still visible, then it's a system dialog.
• Don't enter your credentials into a popup, instead, dismiss it, and open the Settings app manually.
You can read the full research here.
© Copyright IBTimes 2025. All rights reserved.






















