Trickbot malware hits more than 40 countries – and your bank account is at risk
IBM said that Trickbot has spread quickly to dozens of countries and language zones.

A notorious computer Trojan which can be used by cybercriminals to drain bank accounts is now active in more than 40 countries across the world, researchers have found.
The malicious software – known as "Trickbot" – was most recently spotted infecting machines across Latin America including Argentina, Chile, Colombia and Peru, according to Limor Kessem, a security expert at IBM's X-Force division, in an analysis this week (11 October).
The number of infections in Latin America remains small, but IBM researchers believe that such a strategy is run-of-the-mill for the cybercrime gang responsible, which is known to "test the waters" before adding local banks to its list of official targets.
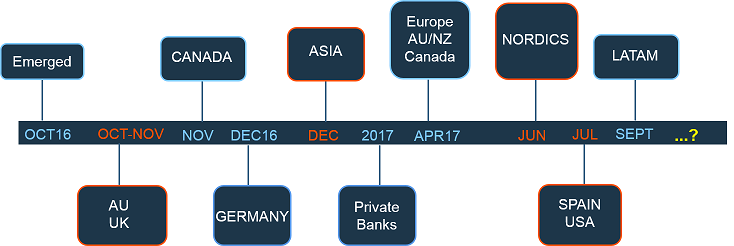
Trickbot first came to light in October 2016 after it hit financial institutions across Asia and Australia, later evolving to target the UK, Germany and Canada.
It launches "redirection" cyberattacks via spam emails in order to send victims to a booby-trapped websites posing as the legitimate banking services.
Targeted individuals – if duped – enter their usernames and passwords into the fake websites which, in reality, send their credentials straight to the criminals.
In its research, IBM said Trickbot has spread quickly to dozens of countries and language zones.
At current count, experts found that it is targeting banks in more than 40 countries spanning Asia, Europe, North America, South America, Australia and New Zealand.
"The TrickBot Trojan is an evolving malware project that appears to have funding and alliances in the cybercrime arena," Kessem wrote in a blog post.
"Its targets are mostly business banking, wealth management and private banking services, which means that the malware's operators are after corporate money and hefty illicit profits. This gang is [...] organised, international and unlikely to disappear anytime soon."
Previously, a version of the Trojan was spotted with worm-like capabilities by Flashpoint, a cybersecurity firm. It was designed to spread in the same fashion as "WannaCry" and "NotPetya", two ransomware strains which both caused global chaos earlier this year.
That hasn't happened yet, but that doesn't mean the Trojan is not a threat, IBM said.
In September this year, the company said a botnet called "Necurs" - which spread the malware globally - helped to spew out more than 40 million emails containing Trickbot.
The research also suggested that the cybercriminals behind the attacks have been "experimenting with other ideas," These include serving up the Trojan directly from fake banking websites and using new types of malicious code to illicitly mine cryptocurrency from victims' machines.
The identities of those behind the scheme remain a mystery.